# DNS
The Domain Name System is a hierarchical and decentralized naming system for computers, services, or other resources connected to the Internet or a private network.
It associates various information with domain names assigned to each of the participating entities.
# Two types of role
# 1 - Authoritative
Authoritative means the server is responsible for a (or several) zone(s). It is the only one (master + slaves (if exists)) which contains the records of this zone ! It's a part of the global dns database.
Example of technologies which support authoritative role by design (not by using plugin, config trick or whatever) :
- Bindopen in new window by ISCopen in new window
- NSDopen in new window by NL netlabsopen in new window
- PowerDNS Recursoropen in new window by OXopen in new window
- Knotopen in new window by CZ.NICopen in new window
# 2 - Recusrive
Example of technologies which support recursive role by design (not by using plugin, config trick or whatever) :
- Bindopen in new window by ISCopen in new window
- [Unbound](https://en.wikipedia.org/wiki/Unbound_(DNS_server) by NL netlabsopen in new window
- PowerDNS Recursoropen in new window by OXopen in new window
# Implementation
# Bind9
Bind is both an authoritative AND recursive domain main server
https://wiki.csnu.org/index.php/Installation_et_configuration_de_bind9
the process name of bind9 is "named"
# rndc (bind runtime management tool)
name server control utility
Write (dump) cache of named in default file (/var/cache/bind/named_dump.db)
dumpdb [-all|-cache|-zones|-adb|-bad|-fail] [view ...]
rndc dumpdb -cache default_any
enable query logging in default location (/var/log/bind9/query.log)
rndc querylog [on|off]
toggle querylog mode
rndc querylog
flush Flushes all of the server's caches.
rndc flush
flush [view] Flushes the server's cache for a view.
rndc flush default_any
get unic master zone loaded
named-checkconf -z 2> /dev/null | grep 'zone' | sort -u | awk '{print $2}' | rev | cut --delimiter=/ -f2 | rev | sort -u
named-checkconf -z 2> /dev/null | grep 'zone' | grep -v 'bad\|errors' | sort -u | awk '{print $2}' | rev | cut --delimiter=/ -f2 | rev | sort -u
2
keep cache
systemctl reload bind9
empty cache
systemctl restart bind9
### Knot
# Troubleshooting command
Manually trigger a zone transfer from master to slave.
To run on slave side
knotc zone-retransfer example.org
Reload a zone from a disk and send NOTIFY to slave.
To run on master side
knotc zone-reload example.org
# NSD
I advice you to check the fellow's tutorial
https://toutetrien.lithio.fr/article/installer-son-serveur-dns-faisant-autorite-avec-nsd
# Record types
# CAA
CAA stands for Certificate Authority Authorization
I.e. : Which CA do you allow to deliver certificate for your domain ?
How to generate your CAA record, for both wildcard + non-wildcard certificate common name.
https://sslmate.com/caa/
# Query a dns server
dig
dig @8.8.8.8 +short +notcp google.com
dig @8.8.8.8 +noall +answer +tcp example.org A
dig @8.8.8.8 +noall +answer +notcp example.org A
dig @8.8.8.8 google.com +short +subnet=192.168.1.0/24
dig @8.8.8.8 google.com +short +subnet=10.0.0.0/8
dig @8.8.8.8 +short example.org +nodnssec
2
3
4
5
6
7
8
others options
- +short
- +(no)tcp
- +(no)dnssec
- +noall
- +answer
- type
# DNSSEC
- Only one key is known and trusted by all resolver of the world. (The one of the
.) - We have to think with
zones
Each zone contains :
- KSK : Key signing Key
- ZSK : Zone signing Key (signed by KSK)
- DS : (record DNS) Delegation Signer Each KSK digest of a given zone is contained in the parent zone
Si DNSSEC non activé, alors record NSEC3 ajouté (en auto souvent) dans la zone parente. (Preuve de non existence de la signature du domaine, pour ne pas faire fail le DNSSEC)
# SoftHSM
softhsm : s'occupe de la gestion des clefs (stockage, generation, signature des ZSK par la KSK)
Exemple : https://dnsviz.net/d/lithio.fr/dnssec/
ods-enforcer key list --verbose --all --zone lithio.fr
Keys:
Zone: Keytype: State: Date of next transition: Size: Algorithm: CKA_ID: Repository: KeyTag:
lithio.fr KSK active 2020-04-24 05:26:19 2048 8 f88125e010c6c1ad671df83048f877f8 SoftHSM 65035
lithio.fr ZSK retire 2020-04-24 05:26:19 1024 8 06ecab532b0b27c8ef2f17d6624c51d1 SoftHSM 65121
lithio.fr ZSK ready 2020-04-24 05:26:19 1024 8 89087g092480f25470ce515c780ca373 SoftHSM 8685
2
3
4
5
6
# Public Resolver classic flow
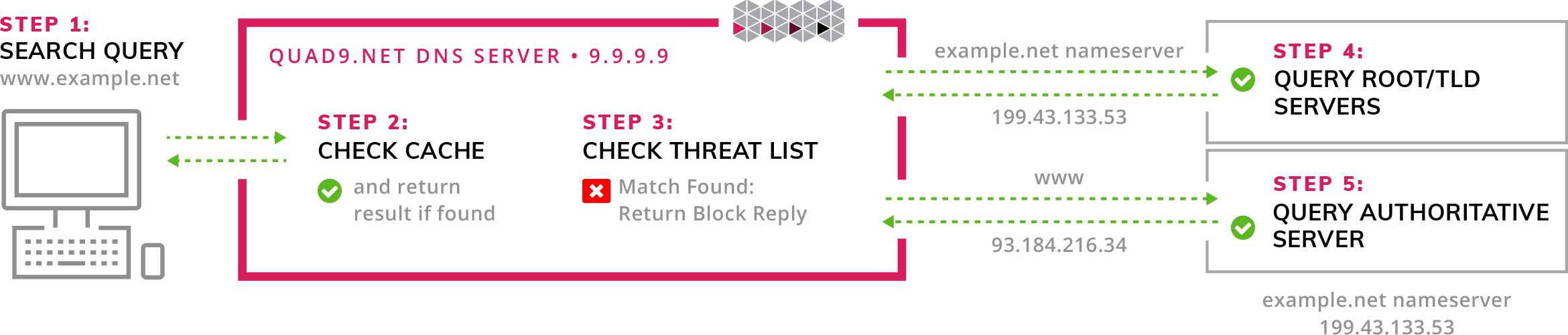
# Stub zone
A stub zone can ONLY be configured on a recursive server. This mecanism is intended to boost zone delegation, by avoiding to start again recursion process from root servers.
If you know the authoritative nameserver for a given zone you can avoid recursion process (because you already known, no need to discover).
For unbound.conf you can setup something like this :
stub-zone:
name: "dyn.example.com"
stub-addr: 10.10.10.10,10.10.10.11
2
3
# Zone delegation
To be updated...
# Performance test
DNS queryperf, un programme de mesure de performance, qui est distribué avec BIND (dans le répertoire contrib/).
Sur une Debian, queryperf peut s'installer ainsi :
# Build queryperf tool
cd /tmp
apt-get source bind9
cd bind9-9.4.2/contrib/queryperf
./configure
make
# Pas de cible install dans le Makefile
sudo cp queryperf /usr/local/sbin
2
3
4
5
6
7
Nous pouvons maintenant le lancer pour voir les options (je n'ai pas tout montré) :
Usage: queryperf [-d datafile] [-s server_addr] [-p port] [-q num_queries]
[-b bufsize] [-t timeout] [-n] [-l limit] [-f family] [-1]
[-i interval] [-r arraysize] [-u unit] [-H histfile]
[-T qps] [-e] [-D] [-c] [-v] [-h]
-d specifies the input data file (default: stdin)
-s sets the server to query (default: 127.0.0.1)
-q specifies the maximum number of queries outstanding (default: 20)
-t specifies the timeout for query completion in seconds (default: 5)
2
3
4
5
6
7
8
# Create your record list
In order to have an input file to give to queryperf
Form du fichier
www.0fjtvn3q0i.example A
www.ngw7m3vq71.example A
www.2u1.example A
2
3
# Run
./queryperf -d example.com.list -s 10.10.10.10
Sources : Stephane Bortzmeyeropen in new window
# Security
Web script injection via DNS
dig avalz.it TXT +short
"<script>alert(\"hi!\")</script>"
2
Try by yourself on weak website : https://dnslookup.online/
# Root servers
https://root-servers.org/index.html
# Name convention proposal
# Private zone
node.fonction.env.tld
ceph casegw1.s3.prod.example.comgw2.s3.prod.example.comgw.s3.prod.example.coms3.prod.example.com CNAME gw.s3.prod.example.com
mon1.s3.prod.example.common2.s3.prod.example.common3.s3.prod.example.com
gw1.s3.staging.example.comgw2.s3.staging.example.common1.s3.staging.example.common2.s3.staging.example.common3.s3.staging.example.com
gw1.s3.dev.example.comgw2.s3.dev.example.common1.s3.dev.example.common2.s3.dev.example.common3.s3.dev.example.com
MinIO caseclient.s3.prod.example.comclient.s3.staging.example.comclient.s3.dev.example.com
Oio caseclient.s3.prod.example.comclient.s3.staging.example.comclient.s3.dev.example.com
# Resources
https://www.dnsperf.com/dns-providers-list/
